Structure of a Domain in Active Directory. Discover the essentials of Active Directory (AD), a critical component for managing network environments. Learn about its key elements such as Organizational Units (OUs), groups, users, and computers. Understand the role of domain controllers, the importance of hierarchical structuring, and how Group Policy enhances security and management efficiency. Explore best practices for AD management, including automation with PowerShell, maintaining an organized structure, enforcing strong security policies, and leveraging advanced auditing tools. Stay updated with the latest developments in AD for a robust, secure network infrastructure.
This is 3rd Part / Chapter in Active Directory Tutorial.
Read Previous Posts.
1. Introduction to Active Directory | Active Directory Tutorial
2. Active Directory Domain Services (ADDS) | Active Directory Tutorial
Structure of a Domain in Active Directory
Table of Contents

Basic Concepts of a Domain in Active Directory
A domain within Active Directory (AD) forms the cornerstone of network security and administration. It is essentially a logical grouping of objects that include users, groups, and devices. Each domain contains these objects and shares the same Active Directory database and security policies, providing a cohesive and centralized administration structure.
The primary benefit of using a domain in Active Directory is the centralization of administration. By organizing objects into a domain, network administrators gain the ability to streamline management tasks, enforce uniform security protocols, and implement policies efficiently. This simplification is crucial for large organizations, as it reduces the complexity inherent in managing multiple users and devices across various geographical locations.
At the heart of a domain is the domain controller. A domain controller is a server that responds to security authentication requests within the domain, effectively acting as the gatekeeper for access to network resources. It maintains the AD database, ensuring that all changes are propagated across the network. In environments where high availability and fault tolerance are needed, multiple domain controllers can be employed, providing redundancy and load balancing for authentication requests.
Moreover, a domain in Active Directory not only centralizes user and device management but also enhances security. Policies related to user authentication, password management, and access control can be uniformly applied across the domain. This ensures consistency and compliance with organizational and regulatory standards, minimizing security risks.
In conclusion, understanding the fundamental aspects of a domain in Active Directory is crucial for efficient network management. By leveraging the centralized administration capabilities and robust security features offered by domains and domain controllers, organizations can maintain an organized, secure, and efficient IT environment.

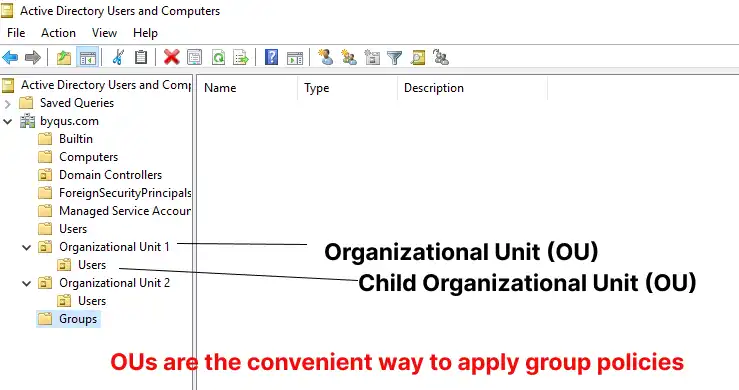
Organizational Units (OU) in Active Directory
Organizational Units (OUs) are a fundamental element within Active Directory that play a crucial role in logically organizing and managing resources. Essentially, OUs serve as containers that house different objects such as users, groups, computers, and other OUs. By leveraging OUs, administrators can create a hierarchical structure that mirrors the organization’s functional or geographical design.
The hierarchical nature of OUs allows for the segregation of resources in a manner that reflects the specific management needs and policies of distinct departments or divisions. This structuring simplifies administrative tasks by permitting administrators to delegate permissions at various levels. For instance, an IT administrator can grant certain control privileges to department heads, enabling them to manage their distinct sections without affecting the broader Active Directory environment.
This delegation is essential for ensuring that administrative tasks are both efficient and secure. By granting permissions strictly within the confinements of particular OUs, organizations can maintain a high level of control while distributing workload responsibilities. Such targeted administrative powers enhance operational efficiency and minimize potential risks associated with unrestricted administrative access.
Additionally, within the framework of OUs, Group Policy Objects (GPOs) play a pivotal role. GPOs are pivotal mechanisms for implementing specific policies and configurations across a wide array of Active Directory objects within OUs. Whether it’s setting security policies, installing software, or configuring user environments, GPOs enable administrators to enforce consistent settings throughout the organization. By attaching GPOs to particular OUs, administrators can tailor policies that meet the unique needs of different organizational segments.
In summary, OUs in Active Directory are essential for structuring and managing resources efficiently. They facilitate effective delegation of administrative tasks and the application of Group Policy Objects, thus ensuring that organizational management is both systematic and secure.
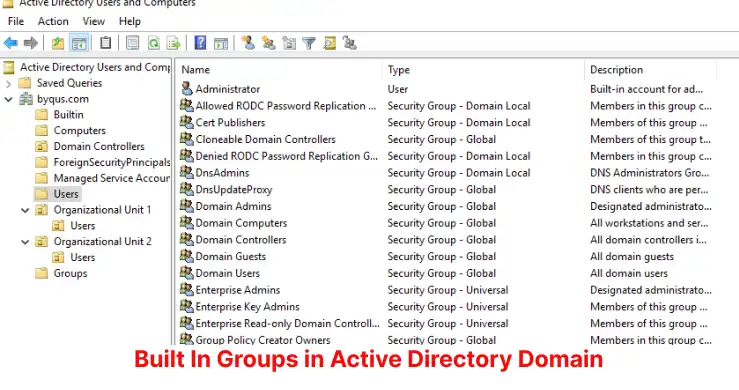
Groups in Active Directory
In Active Directory, groups are essential components utilized to streamline user management and resource access. Primarily, there are two types of groups in Active Directory: security groups and distribution groups. Security groups are pivotal in assigning permissions to a range of resources such as files, folders, and shared drives. On the other hand, distribution groups are mainly used for email distribution lists within an organization.
Using groups to manage permissions simplifies administrative tasks significantly. Instead of configuring permissions for each user individually, administrators can assign permissions to groups, subsequently applying them to all members of that group. This efficiency is further enhanced through the practice of nesting groups, where a group can be a member of another group. Nesting groups allows for conserving administrative resources and maintaining a more organized permission structure. For instance, if a security policy needs amending, adjusting it within a top-level group automatically updates permissions for all nested groups and their members.
Groups in Active Directory also have distinct scopes, which define their span of influence. The three primary scopes are domain local, global, and universal. Domain local groups are restricted to granting permissions within a single domain, making them suitable for managing resources specific to that domain. Global groups, in contrast, can contain user accounts and groups from within the same domain but can be used to grant permissions in any domain within the forest. Universal groups are the most expansive, capable of containing users and groups from any domain in the forest, which can also be assigned permissions across any domain. This wide scope makes universal groups apt for roles that require broad access across multiple domains.
Understanding and effectively utilizing the various types of groups and scopes in Active Directory is crucial for efficient resource management and security enforcement. Proper group management not only helps in organizing user permissions adequately but also aids in reducing redundancy and enhancing overall administrative efficacy.
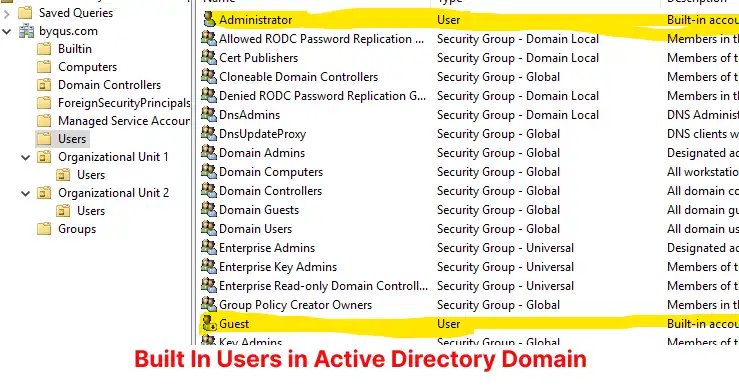
User Objects in Active Directory
User objects in Active Directory (AD) are pivotal elements that encapsulate the digital identity of individuals within a network. These objects serve multiple essential functions including authentication, authorization, and granular control over user account policies and profiles. Comprehending the role and attributes of user objects helps streamline network management and fortify security protocols.
Creation and management of user objects are central to the efficacy of Active Directory. New user accounts can be added using various graphical interfaces, such as the Active Directory Users and Computers (ADUC) console or programmed via scripts for automation. These accounts embody a unique username that acts as an identifier within the domain. Mandatory attributes assigned during the account creation include the user’s full name and logon name.
Equally critical are password policies associated with user objects. Administrators are empowered to enforce stringent security policies that dictate password complexity, history, and expiration. These rules help safeguard against unauthorized access and potential security breaches.
Status of user accounts is another crucial consideration. User objects may be active, disabled, or locked based on the operational requirements or security incidents. For instance, disabling an account immediately halts access without deleting the object, which is useful in cases such as an employee leaving the organization temporarily.
User attributes form the backbone of personalization and control in AD. Besides usernames and password policies, attributes like email addresses, department, and job titles can be added to enhance the directory’s utility. Profile settings manage individual user environments, including home directories and desktop configurations, ensuring a tailored experience for each user on any domain-joined machine within the network.
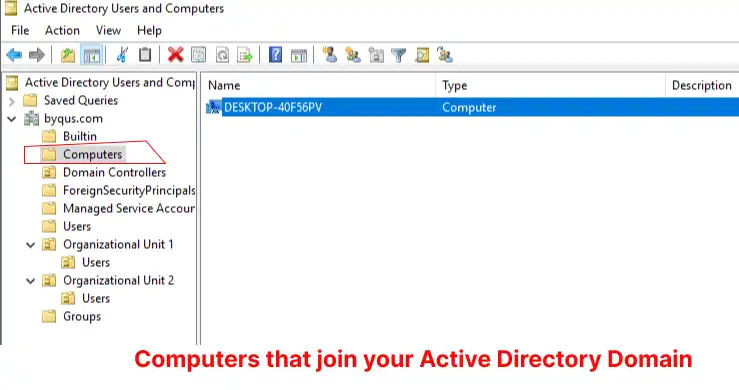
Computer Objects in Active Directory
In Active Directory (AD), computer objects are crucial components that represent physical or virtual machines within a domain. These objects serve a pivotal role in the centralized management of computer accounts, ensuring streamlined access control, consistent policy enforcement, and enhanced security compliance across an organization’s network. Each computer object in AD corresponds to a distinct computer account, embodying attributes that identify and define its associated machine.
One significant aspect of computer objects in AD is their ability to secure access through authentication and authorization processes. When a computer joins a domain, it essentially becomes a recognized entity within that domain, earning a unique Security Identifier (SID). This process, known as domain-joining, is fundamental for ensuring that only authenticated computers can interact with domain resources. Consequently, domain-joined computers benefit from centralized user account management and are subject to security policies enforced by Group Policy.
Group Policy plays a pivotal role in managing computer-specific settings within a domain. Administrators can implement a wide array of policies, tailoring configurations such as software deployment, security settings, and user permissions, thereby creating a standardized computing environment. For instance, through Group Policy, IT departments can enforce password complexity rules, configure automatic updates, and control access to network shares, all from a single administrative console. This level of control is essential for maintaining network integrity and safeguarding sensitive data.
Additionally, the centralized management of computer objects in AD facilitates efficient monitoring, auditing, and reporting. Administrators gain visibility into the status and activities of all domain-joined computers, enabling proactive management of security threats and system compliance. Through tools such as Active Directory Users and Computers (ADUC) and PowerShell scripts, administrators can perform bulk updates, manage group memberships, and troubleshoot issues effectively.
In summary, computer objects in Active Directory are indispensable for modern IT environments, offering robust mechanisms to manage, secure, and standardize computer configurations within a domain. Their integration with Group Policy and centralized management capabilities underscores their importance in sustaining a secure and efficient network infrastructure.
Active Directory (AD) is a critical component in managing a network environment, and the effective management of Active Directory objects is paramount to maintaining a secure and efficient system. The key objects managed within AD include Organizational Units (OUs), groups, users, and computers. Understanding the intricacies of creating, organizing, and managing these objects can significantly streamline administrative tasks.
Creating and Organizing Active Directory Objects
When creating AD objects, it is essential to follow a well-structured naming convention to avoid confusion and facilitate easy identification. For Organizational Units (OUs), it is advisable to design a hierarchy that mirrors the structure of the organization, such as by departments or geographical locations. This hierarchical structure helps in applying group policies at different levels and simplifies delegation of administrative rights.
Groups in Active Directory can be categorized into two major types: security groups and distribution groups. Security groups are used to assign permissions to resources within the network, while distribution groups are primarily used for email distribution lists. It is a best practice to use groups rather than individual users when assigning permissions, as this simplifies management and enhances security.
For user accounts, it is recommended to establish a standard procedure for creating usernames, such as using an employee’s first initial and last name, to maintain consistency. Moreover, the use of templates can expedite the process of creating user accounts with similar attributes.
Automation with Scripts and Tools
Automation is a powerful tool in managing Active Directory objects efficiently. Using PowerShell scripts, administrators can automate repetitive tasks such as creating user accounts, resetting passwords, or updating group memberships. Tools like Group Policy Management Console (GPMC) and Active Directory Administrative Center (ADAC) provide an intuitive interface for managing AD objects and policies.
Common Administrative Tasks
Managing AD objects often involves performing routine tasks such as moving objects between OUs, changing group memberships, and enforcing policies. Moving objects can be done via the AD Users and Computers console or using PowerShell cmdlets for bulk operations. Regular audits of group memberships ensure that users have appropriate access levels and help in identifying any potential security risks.
Enforcing policies through Group Policy Objects (GPOs) enables administrators to apply settings across the entire domain or specific OUs. This includes security settings, software installations, and script execution at startup or login. Consistently reviewing and updating GPOs is crucial to maintaining compliance and security within the IT environment.
Conclusion and Best Practices
Understanding the structure of a domain in Active Directory (AD) is fundamental for maintaining an organized, secure, and efficient network environment. This article has provided an in-depth look at the critical components of Active Directory, including domain controllers, organizational units, and group policies. These elements form the backbone of a well-structured AD infrastructure, allowing for streamlined management and enhanced security.
Implementing best practices for Active Directory management is essential to maintaining operational efficiency and security. First and foremost, regularly review and update group policies to ensure they reflect current organizational needs and security standards. Keeping documentation up to date can also greatly assist in managing changes and troubleshooting issues.
Security management is another critical aspect. Ensure you enforce strong password policies and regularly update passwords. Multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for unauthorized users to gain access. Using advanced auditing and monitoring tools helps in detecting and responding to suspicious activities promptly.
Maintaining an organized AD structure involves periodically cleaning up unused accounts and group memberships, which can accumulate and complicate maintenance. Implementing a standardized naming convention for objects within Active Directory can also contribute to a more organized system, aiding in easier navigation and management.
To keep the Active Directory environment healthy, consider regular backups and disaster recovery planning. Regularly testing backup restoration processes ensures that backups are reliable and perform as expected during an actual recovery scenario.
For those looking to deepen their understanding of Active Directory and stay updated with the latest developments, numerous resources are available. These include official documentation from Microsoft, community forums, and professional courses. Staying engaged with the AD community through webinars and industry conferences can also provide valuable insights and updates.
By following these best practices, organizations can ensure their Active Directory infrastructure remains robust, secure, and efficient, effectively supporting their IT and business operations.




