What Is a Domain in Active Directory?. Active Directory is one of the most powerful and widely used identity and access management systems in the world. Whether an organization has 50 users or 50,000, AD becomes the backbone that manages user identities, device authentication, security policies, and access to resources. But to truly understand how Active Directory works, you must first understand the building blocks that hold it together.
In the previous articles of this series, we explored the Introduction to Active Directory, where we broke down the purpose of AD, how it is used in modern organizations, and why identity management is the foundation of enterprise security. We also covered What Is a Forest in Active Directory?, where you learned that a forest is the top-level logical structure — the entire kingdom of Active Directory — governing trust relationships, schema, and the overall directory configuration.
According to Microsoft documentation, Active Directory domains act as the primary administrative and security boundary for identity management in Windows environments.
Microsoft Learn → Domains and forests
In modern IT environments, especially those supporting hundreds or thousands of users, identity is the foundation of everything — access, security, compliance, and auditing. Active Directory domains were created to solve this exact problem: how to control identities and resources at scale without chaos.
To understand why domains still matter today (even in cloud-first organizations), we must look at the practical problems they were designed to solve.
Now, we take the next step into the most practical and commonly encountered component of Active Directory: the Domain.
If a forest is the entire world of Active Directory, the domain is the country where day-to-day identity life happens. It is inside domains that users log in, computers join the directory, administrators apply policies, and IT teams manage everything from passwords to access rights.
Understanding what a domain is — and why it exists — is essential before moving into key topics such as Domain Controllers, Organizational Units (OUs), Sites, Replication, and eventually Group Policies.
This article will guide you through:
- What exactly a domain is
- Why domains were created
- How domains manage identity and security
- What objects live inside a domain
- How domains differ from forests
- Real-world examples of domain structures
- Why domains are so important for IT governance
By the end of this post, you will have a clear and confident understanding of what a domain is and how it forms the backbone of every Active Directory environment.
And as always — if you want to continue mastering AD, don’t forget to explore more topics in our Active Directory Series.
This article is the next installment in our Active Directory Series.
If you missed the previous chapters, start here:
Understanding Domains is essential before moving into topics like Domain Controllers, OUs, Sites, and Group Policy. Let’s begin.
What Is a Domain in Active Directory?
What Is a Domain in Active Directory?
A domain in Active Directory is one of the core building blocks of Microsoft’s identity and access management framework. It acts as a logical, administrative, and security boundary that helps organizations organize and control thousands of users, devices, groups, and applications in a structured way.
You can think of a domain as the home where all identity objects live and operate under a single set of authentication and security rules. It provides a unified environment where administrators can centrally manage logins, enforce policies, delegate administrative rights, and secure access to resources such as file shares, printers, and applications.
A domain is essential for any Windows-based enterprise network because it standardizes how identities are created, authenticated, and governed. When a user signs in to their computer, accesses a shared folder, or tries to join a device to the network, the domain defines how their identity is verified and what they’re allowed to do.
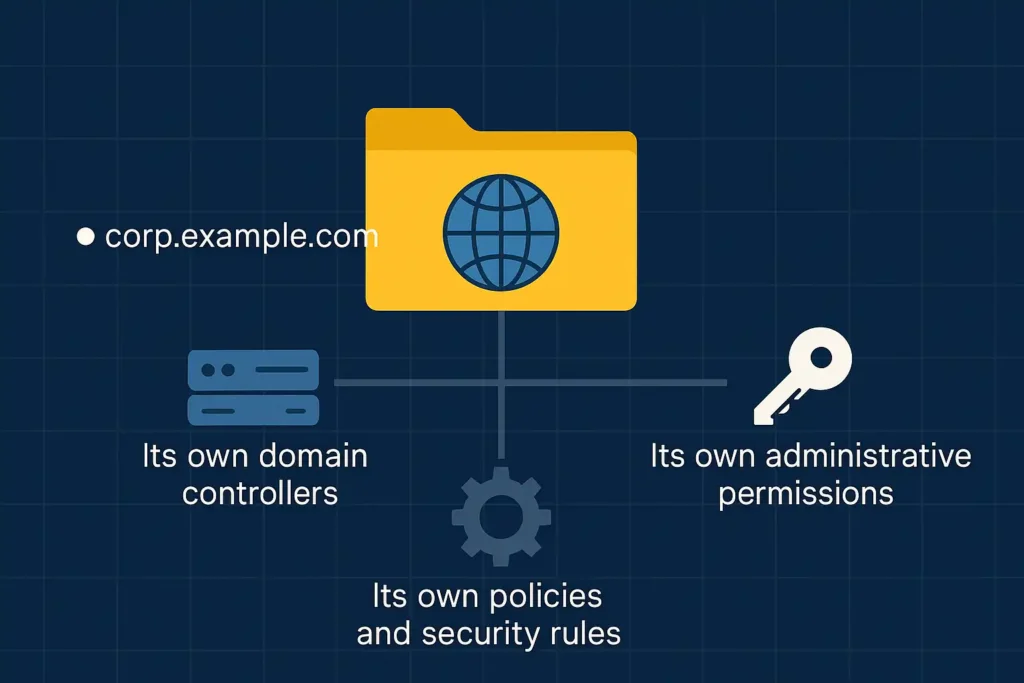
Core Components of an Active Directory Domain
Every Active Directory domain is built on a defined set of components that together enable centralized identity management, security enforcement, and administrative control.
1. A Unique DNS Name
Each domain is identified by a DNS-based namespace, such as:
corp.example.comthepoemstory.localcontoso.com
This DNS name uniquely identifies the domain within the network and plays a critical role in authentication.
User identities are directly tied to the domain namespace, forming login identities such as:
john.doe@corp.example.com
Beyond identification, the domain DNS name enables service discovery, authentication routing, and trust relationships within and across domains.2. Domain Controllers (DCs)
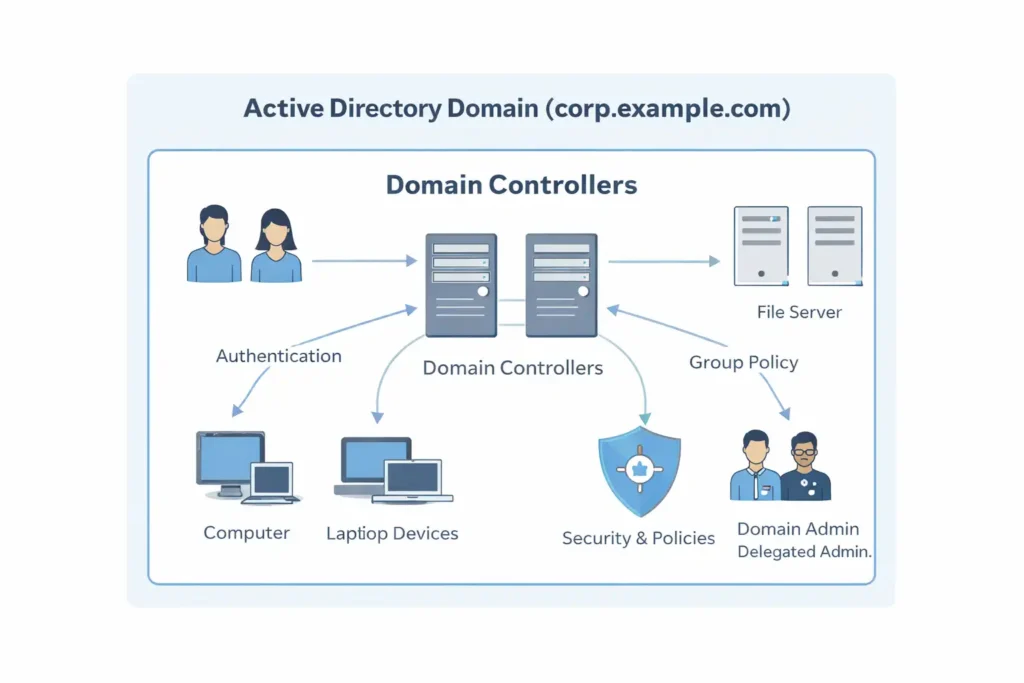
A domain operates through one or more Domain Controllers (DCs) — the servers that host the Active Directory database and enforce all authentication and authorization decisions.
Domain Controllers are responsible for:
- Authenticating user and device logins
- Processing password changes
- Validating group memberships
- Handling Kerberos and NTLM authentication
- Delivering security and configuration policies through Group Policy
Without Domain Controllers, a domain cannot authenticate users, apply policies, or function as a security boundary.
3. Domain-Specific Policies and Security Rules
Each domain maintains its own independent set of security and configuration controls, including:
- Password and authentication policies
- Account lockout thresholds
- Group Policy Objects (GPOs)
- Access control and authorization rules
This design allows multiple domains within the same forest to operate under different security standards, supporting diverse business, regulatory, or geographic requirements.
4. Its Own Administrative Permissions
A domain is also a boundary for administrative authority. A domain also defines a clear administrative boundary.
Within a domain, administrators can:
- Create and manage user, group, and computer accounts
- Deploy and manage Group Policies
- Control access to applications and resources
- Delegate administrative responsibilities to specific teams
- Enforce compliance and security controls
This separation of administrative authority makes domains especially valuable in large or distributed organizations where centralized control and delegated management must coexist.
Why This Matters
Domains provide structure, security, and control.
They define who can sign in, what resources can be accessed, and how security policies are enforced across an organization. Without domains, identity management becomes fragmented, policies become inconsistent, and security risks increase significantly.
Whether an organization supports 50 users or 50,000, a well-designed domain ensures that identity and access management remains centralized, scalable, and secure.
Why Do Domains Exist?
Domains exist because identity, security, and access management do not scale naturally without structure. As organizations grow, managing users, devices, and permissions individually becomes not only inefficient, but dangerous. Domains were created to solve this exact problem: how to centrally control access and security across large, distributed IT environments.
Without a domain, every computer must be configured and secured independently. User accounts exist locally on individual machines, policies vary from system to system, and enforcing consistent security standards becomes nearly impossible. This leads to configuration drift, weak security controls, administrative overload, and a significantly higher risk of breaches.
A domain provides a single, unified framework that centralizes identity, authentication, policy enforcement, and administration. It transforms a complex collection of computers and users into a cohesive, manageable, and secure system, where control flows from a trusted central authority.
Below are the key reasons domains are essential in modern IT environments.
1. Centralized Authentication for All Users and Devices
In a domain, every user logs in using a single identity that is stored and managed centrally.
At the heart of a domain is centralized authentication.
Instead of maintaining separate user accounts on every device, a domain stores all identities in a central directory. Each user logs in using a single domain identity, which is validated by trusted Domain Controllers.
This enables:
- One username and password to work across the entire network
- Central enforcement of password complexity and expiration rules
- Integration of advanced authentication methods such as MFA
- Secure credential validation using standardized protocols
- Full traceability of authentication events for auditing and security monitoring
By eliminating local accounts and decentralized credentials, domains ensure that identity management remains consistent, controlled, and secure, even across thousands of users and devices.
2. Centralized Policy Enforcement Across the Domain
Domains allow organizations to enforce consistent security and configuration policies using Group Policy Objects (GPOs).
Rather than configuring each machine manually, administrators define policies once and apply them automatically across the domain. These policies can govern:
- Password and lockout requirements
- Firewall and endpoint security settings
- Software installation and application restrictions
- Desktop configuration and user environment behavior
- System hardening and compliance controls
This centralized approach ensures that every domain-joined device follows the same standards, reducing misconfigurations and human error. Changes can be deployed instantly at scale, saving time while improving security posture.
3. Delegated Administration Without Losing Control
Large organizations cannot function with a single all-powerful administrator. Domains solve this by enabling granular delegation of administrative responsibilities.
Within a domain, permissions can be assigned precisely so that teams manage only what they are responsible for. For example:
- Helpdesk staff can reset user passwords
- HR teams can update user attributes
- Department administrators can manage group memberships
- IT security teams can control policies and auditing
All of this is achieved without granting full Domain Admin rights, preserving security boundaries and minimizing risk. Delegation allows organizations to scale operations efficiently while maintaining strict oversight and accountability.
4. Strong Security Boundaries for Access Control
A domain establishes a clear and enforceable security boundary.
It defines:
- Who is allowed to authenticate
- Which resources users can access
- What permissions are granted
- How authentication and authorization decisions are made
Access to resources such as file servers, applications, and systems is determined by centrally managed policies and group memberships. This ensures that users can access only what they are explicitly permitted to, protecting sensitive data and limiting the blast radius of potential compromises.
Domains also provide the foundation for auditing, compliance reporting, and incident investigation by centralizing logs and access records.
In Short
Domains exist to ensure that complex IT environments remain:
- Organized — through centralized identity and structure
- Secure — through consistent authentication and policy enforcement
- Standardized — through uniform configuration and controls
- Efficient to manage — through automation and delegation
- Scalable — capable of supporting future growth without chaos
They form the backbone of identity and access management in any Windows-based enterprise and continue to play a critical role even in modern hybrid and cloud-integrated environments.
What Objects Exist Inside a Domain?
An Active Directory domain is more than just a security boundary—it is a centralized directory of identity and resource objects. These objects represent every user, device, service, and logical grouping that participates in authentication, authorization, and management within the domain.
All objects inside a domain are governed by the domain’s authentication mechanisms, security policies, and administrative rules, ensuring consistency and control across the environment.
Below is a detailed look at the key object types that exist inside a domain.
- Users
- Computers
- Groups
- Organizational Units (OUs)
- Service and application accounts
- Shared resources like printers and file servers
All these objects follow the policies and authentication rules of the domain.
1. User Accounts
User accounts represent individual people or identities that require access to domain resources.
User objects are used to:
- Authenticate users when they sign in
- Assign permissions to files, applications, and services
- Apply security and configuration policies
- Track activity for auditing and compliance
Each user account is uniquely identified within the domain and can be:
- Enabled or disabled centrally
- Assigned to security or distribution groups
- Subject to password policies, MFA, and access restrictions
By managing users centrally, domains eliminate the need for separate local accounts on individual machines.
2. Computer Accounts
Every device that joins a domain—such as desktops, laptops, and servers—creates a computer account in Active Directory.
Computer accounts:
- Allow devices to authenticate securely to the domain
- Enable centralized policy application through Group Policy
- Establish trust between the device and Domain Controllers
- Support secure communication using Kerberos
This ensures that only authorized, domain-joined devices can access protected network resources.
3. Groups
Groups are used to simplify access management by assigning permissions to collections of users or devices rather than individuals.
There are two primary types of groups:
- Security groups — used for access control and permissions
- Distribution groups — used for email communication
Groups enable:
- Scalable permission management
- Role-based access control
- Simplified onboarding and offboarding processes
Instead of managing permissions user by user, administrators assign access once to a group.
4. Organizational Units (OUs)
Organizational Units (OUs) are logical containers used to organize objects within a domain.
OUs allow administrators to:
- Structure users and computers by department, location, or function
- Apply Group Policies selectively
- Delegate administrative control to specific teams
- Simplify management in large environments
Unlike groups, OUs are not used for permissions but for organization, policy application, and delegation.
5. Service and Application Accounts
Service accounts represent applications, services, or automated processes that require authentication within the domain.
These accounts are used by:
- Windows services
- Scheduled tasks
- Enterprise applications
- Backend processes
Service accounts enable secure, auditable authentication without using personal user credentials. Modern best practices favor managed service accounts (gMSA) to improve security and reduce credential exposure.
6. Shared Resources (Printers, File Servers, Applications)
Domains also manage access to shared resources, such as:
- File servers and shared folders
- Network printers
- Internal applications and services
While these resources may not always be directory objects themselves, access to them is controlled through domain identities, groups, and permissions. This ensures consistent access control across the organization.
How These Objects Work Together
All domain objects operate within a unified framework:
- Users and computers authenticate to the domain
- Groups define access and roles
- OUs structure the environment and apply policies
- Service accounts enable automation and applications
- Shared resources enforce access based on domain identities
This interconnected design allows domains to scale cleanly while maintaining security, visibility, and administrative control.
Why This Object Model Matters
By centralizing identities, devices, and resources into a single domain, organizations gain:
- Consistent security enforcement
- Simplified administration
- Strong auditing and compliance capabilities
- Reduced operational complexity
This object-based model is what makes Active Directory domains reliable, scalable, and essential in enterprise environments.
Forest vs Domain: What’s the Difference?
| Forest | Domain |
|---|---|
| The complete Active Directory environment | A subdivision within the forest |
| Defines global structure, schema, and trust | Defines local authentication and policy boundaries |
| Only one forest per deployment | One or multiple domains can exist in a forest |
Analogy: A forest is a city; each domain is a district with its own rules and administrators.
Real-World Examples of Domain Design
Active Directory domains are implemented differently depending on an organization’s size, structure, and operational complexity. Below are the most common real-world scenarios.
Single Domain Environment
A single domain design is most commonly found in small to medium-sized organizations where administrative simplicity and centralized control are the primary goals.
Example:
corp.thepoemstory.com
Where this works best:
- Small and mid-sized businesses
- Organizations with a single IT team
- Minimal regional or regulatory separation
- Centralized security and policy requirements
Key benefits:
- Simple administration and troubleshooting
- Unified security policies across the organization
- Easier Group Policy management
- Lower infrastructure and operational overhead
In a single-domain environment, all users, devices, and resources are managed under one administrative and security boundary, making it easy to maintain consistency and control.
Multi-Domain Environment
A multi-domain design is typically used by large enterprises that require separation based on geography, business units, or regulatory needs.
Example:
apac.company.com
emea.company.com
amer.company.com
Where this is used:
- Global organizations with regional IT teams
- Enterprises with different compliance or legal requirements
- Organizations requiring administrative isolation
- Mergers and acquisitions scenarios
Key advantages:
- Independent security and password policies per domain
- Delegated administration by region or department
- Reduced impact of security incidents across domains
- Scalability for complex organizational structures
Each domain operates as its own administrative and security boundary while still being able to trust and communicate with other domains in the same forest.
Why Domains Matter in Practice
Domains are not just a technical concept—they are the foundation of identity and access management in Windows-based environments.
They are essential for enabling:
🔐 Group Policy (GPOs)
Domains allow administrators to enforce consistent security and configuration policies across users and devices at scale.
📁 Resource Access and Permission Control
Access to file servers, applications, printers, and services is centrally controlled using domain identities and groups.
🛡️ Security Boundaries
Domains define clear authentication and authorization boundaries, limiting unauthorized access and containing security incidents.
🧑💼 Delegated Administration
Administrative responsibilities can be safely distributed across teams without compromising overall control or security.
In Summary
Whether an organization operates with:
- One domain for simplicity
- Multiple domains for scale and separation
Domains provide the structure required to manage identities, enforce security, and scale IT operations reliably.
They remain a critical building block of enterprise identity, even in modern hybrid environments that integrate on-premises Active Directory with cloud identity platforms like Microsoft Entra ID.
What Is a Domain in Active Directory?
🎥 Learn Visually on Our YouTube Channel
Watch detailed video tutorials on Microsoft 365, Entra ID, Azure, and Active Directory directly on our BYQUS YouTube Channel. Get real-world demonstrations, Hindi explanations, and step-by-step guidance from actual admin environments.
📌 Subscribe now and never miss a new IT tutorial — from cloud configuration to troubleshooting and interview preparation.
(FAQ) Frequently Asked Questions on Active Directory
What is a domain in Active Directory?
A domain in Active Directory is a logical and security boundary that groups users, computers, and resources under centralized authentication and management. It allows organizations to control access, enforce security policies, and manage identities from a single trusted framework.
Why are domains important in large organizations?
Domains are essential in large organizations because they provide centralized identity management, consistent security enforcement, and delegated administration. Without domains, managing users and devices individually would be inefficient, error-prone, and insecure.
Can an organization have multiple domains?
Yes. Large enterprises often use multiple domains within a single forest to separate regions, departments, or regulatory requirements. Each domain can have its own security policies while still trusting other domains.
What is the difference between a domain and a forest?
A domain is a single administrative and security boundary, while a forest is a collection of one or more trusted domains that share a common schema and configuration. A forest represents the highest-level boundary in Active Directory.
Do domains still matter in cloud-first environments?
Yes. Domains continue to play a critical role in hybrid identity models, where on-premises Active Directory integrates with cloud identity platforms like Microsoft Entra ID. Many organizations rely on domains for legacy applications, device management, and internal authentication.
What objects exist inside a domain?
A domain contains several identity and resource objects, including:
User accounts
Computer accounts
Groups
Organizational Units (OUs)
Service and application accounts
Shared resources such as file servers and printers
All these objects follow the domain’s authentication and security policies.
Is a domain required for Group Policy?
Yes. Group Policy Objects (GPOs) are applied within the context of a domain. Domains provide the structure and authentication framework required to apply policies consistently across users and devices.
How does a domain improve security?
A domain improves security by enforcing centralized authentication, consistent password policies, access controls, auditing, and role-based administration. It reduces reliance on local accounts and limits unauthorized access to resources.
Can small businesses use Active Directory domains?
Absolutely. Many small and medium-sized businesses use single-domain environments to centralize user management, apply security policies, and simplify administration without the complexity of multi-domain designs.
What happens if a domain controller fails?
If one Domain Controller fails, other available Domain Controllers in the domain can continue authenticating users and enforcing policies. This redundancy ensures high availability and prevents a single point of failure.
Are domains only used with Windows systems?
While domains are native to Windows environments, they can authenticate and manage non-Windows systems, applications, and services using standard protocols such as LDAP and Kerberos.
Is Active Directory being replaced by Entra ID?
No. Microsoft Entra ID does not replace Active Directory; instead, it extends identity to the cloud. Most enterprises use both together in a hybrid model to support modern applications while maintaining on-premises infrastructure.
What is the simplest domain design for beginners?
The simplest design is a single-domain, single-forest model. It is easy to manage, secure, and scale, making it ideal for learning and for small to mid-sized organizations.
Can domains help with compliance and auditing?
Yes. Domains centralize authentication logs, access controls, and policy enforcement, making it easier to meet compliance requirements and perform audits.
When should an organization redesign its domain structure?
Organizations typically redesign domain structures during major growth, mergers and acquisitions, regulatory changes, or when moving to hybrid or cloud-based identity architectures.
In the next article, we’ll explore Domain Controllers, the servers that power authentication, policy enforcement, and trust inside a domain.




