Active Directory (AD) is one of the most important technologies in a Windows-based enterprise environment. It provides a structured and centralized system for managing users, computers, applications, policies, authentication, and permissions across an organization. Introduced with Windows 2000 Server, Active Directory replaced the limitations of NT domains and evolved into a modern identity and access management platform that continues to form the backbone of corporate infrastructure even today.
AD is more than just a directory. It is a complete identity system that ensures the right people have access to the right resources at the right time. It simplifies administrative work by centralizing control, strengthens security through standards-based authentication, and enhances productivity through policy-based automation. Whether an organization is small, medium, or global in scale, Active Directory remains an essential component of IT architecture.
To understand AD deeply, it is important to explore not just what it does, but how it has evolved, why its structure matters, and how administrators can plan and deploy it effectively. This detailed guide will walk you through these core concepts step by step.
Explore: Active Directory Tutorials
Introduction to Active Directory (AD) | Active Directory Tutorial
Overview: What is Active Directory?
Active Directory is a directory service developed by Microsoft that organizes and manages identities and resources in a Windows network. At its core, AD stores information about users, computers, groups, printers, shared folders, servers, and other objects in a secure, hierarchical database. Administrators use this information to authenticate users, authorize access, apply policies, and maintain overall control of the network.
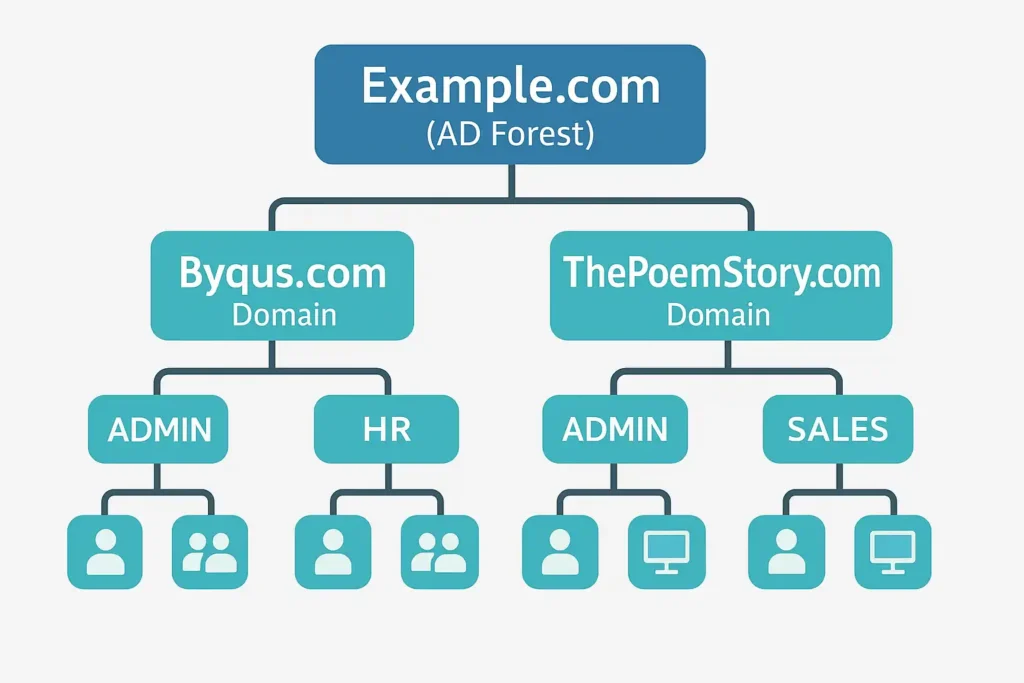
One of the most powerful features of AD is its hierarchical structure. Resources are grouped into domains, domains are grouped into trees, and trees form a forest. This layered system allows organizations of all sizes to create identity boundaries that fit their administrative, geographical, and security needs.
Before AD existed, Microsoft used NT 3.x and NT 4.0 domains, which relied on a Primary Domain Controller (PDC) and one or more Backup Domain Controllers (BDCs). Although that model provided centralized authentication, it lacked scalability and robustness. Only the PDC could accept changes, creating a single point of failure and a bottleneck for large networks.
Active Directory changed all of that. With Windows 2000 Server, Microsoft introduced features such as LDAP-based directory services, multi-master replication, Organizational Units (OUs), Kerberos authentication, Group Policy, and a forest-domain architecture. These advancements transformed identity management into a scalable, manageable, and secure system capable of supporting modern enterprise requirements.
Today, Active Directory operates alongside cloud identity solutions such as Azure Active Directory (Entra ID), enabling hybrid identity environments. While AD continues to manage on-premises devices and legacy applications, Entra ID handles cloud-based services like Microsoft 365, Azure, and SaaS apps — together forming a modern hybrid identity model.
High-Level AD Structure Diagram
Components of Active Directory
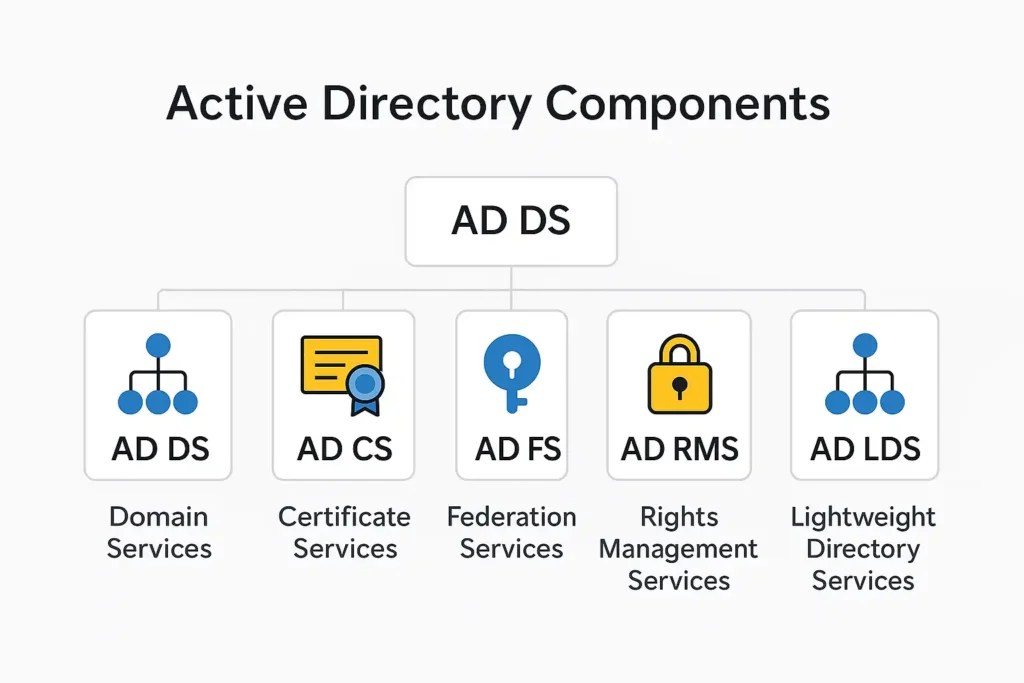
Active Directory is not a single service. It is a collection of specialized components that work together to provide identity, security, authentication, and resource management. Each component has a specific function, and understanding them is crucial for mastering AD.
Active Directory Domain Services (ADDS)
ADDS is the core component of Active Directory. It stores directory data, manages user and computer authentication, and provides the foundation for all other AD services. Every time a user logs in, accesses a shared folder, changes a password, or applies a Group Policy, ADDS is at work.
ADDS uses multi-master replication, meaning all writable Domain Controllers can accept updates and replicate them throughout the domain. This design eliminates the dependency on a single server and makes directory operations more resilient and scalable.
ADDS also introduces the concept of OUs (Organizational Units), which allow administrators to create logical containers for users, computers, and groups. Using OUs, organizations can delegate administrative permissions to different teams without compromising security. Group Policy further enhances this by allowing thousands of configurations to be enforced automatically at the user or computer level.
Active Directory Certificate Services (ADCS)
ADCS provides a full Public Key Infrastructure (PKI) inside the Windows environment. It issues digital certificates used for encryption, authentication, secure email, VPN access, HTTPS, 802.1X Wi-Fi authentication, and smart card logins. Certificates issued by ADCS help ensure secure identity verification across the organization.
A properly configured ADCS environment greatly enhances security, but poor PKI design can cause long-term maintenance challenges. That is why certificate hierarchy planning, CRL distribution, and key management become critical responsibilities.
Active Directory Federation Services (ADFS)
ADFS enables secure Single Sign-On (SSO) across different applications, organizations, and cloud services. It allows users to authenticate locally through AD and access external systems without needing additional passwords. ADFS relies on industry standards like SAML and OAuth to exchange security tokens.
In today’s cloud-first world, many organizations are replacing ADFS with Entra ID-based federation or cloud-based authentication. However, ADFS still plays a crucial role when companies require on-premises SSO or need support for legacy applications.
Active Directory Rights Management Services (ADRMS)
ADRMS provides persistent protection for sensitive documents and emails. Even if someone copies a file outside the network, ADRMS-enforced rules can restrict printing, forwarding, editing, or even screenshot capturing. This makes ADRMS essential for organizations handling confidential or regulated data.
Active Directory Lightweight Directory Services (ADLDS)
ADLDS is a lightweight version of ADDS that provides directory services for applications without requiring a full Active Directory domain. Applications can store configuration or identity data in ADLDS instances without modifying an organization’s production AD schema.
This is useful for software that requires directory-style storage but does not need the full overhead or security boundaries of ADDS.
Benefits of Using Active Directory
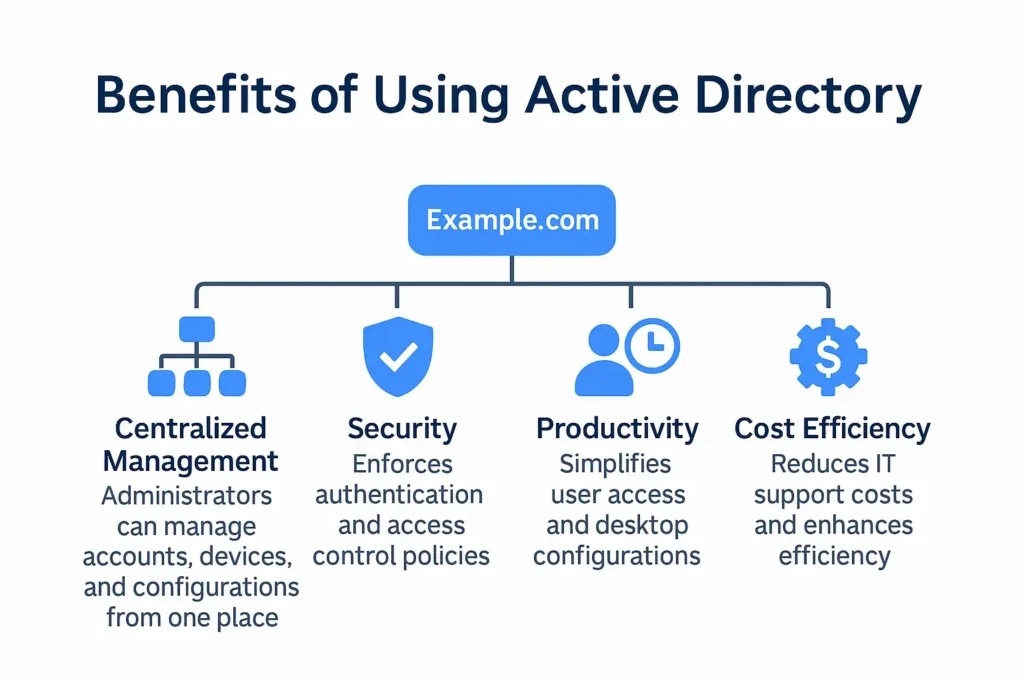
Active Directory brings numerous advantages to enterprise IT environments. The most significant benefit is centralized management. With AD, administrators can control thousands of accounts, devices, and security configurations from a single console. This dramatically reduces the workload and lowers operational risk.
Another major benefit is improved security. AD enforces strong authentication and centralized access control. Group Policy ensures consistent application of security rules, while certificates, smart cards, and conditional access improve identity assurance.
AD also enhances productivity. Through Single Sign-On (SSO), users only need one login to access their resources. Policies ensure consistent desktop configurations. Automated provisioning eliminates manual user setup when employees join or move departments.
Finally, AD is cost-effective. By consolidating identity systems and automating administrative tasks, organizations reduce support costs, shrink security risks, and improve overall IT efficiency.
Use Cases of Active Directory
Active Directory is used across a wide variety of industries and environments. One of the most common uses is identity lifecycle management. Organizations create user accounts when employees join, modify permissions as roles change, and disable accounts when employees leave.
Another major use case is enforcing security policies through Group Policy. Administrators can enforce password complexity, restrict software installations, block USB devices, manage Windows updates, and configure hundreds of settings across all domain-joined devices.
AD also plays a central role in authentication. Every time a user logs in, Kerberos verifies their identity and grants them access to the appropriate resources. This ensures secure and efficient access control.
Integration is another essential use case. AD provides identity and access control for Exchange Server, SharePoint, Teams, System Center, Intune, and many third-party applications.
Regulated industries such as healthcare, finance, and government rely on AD’s auditing capabilities to maintain compliance with standards like HIPAA, SOX, and PCI-DSS.
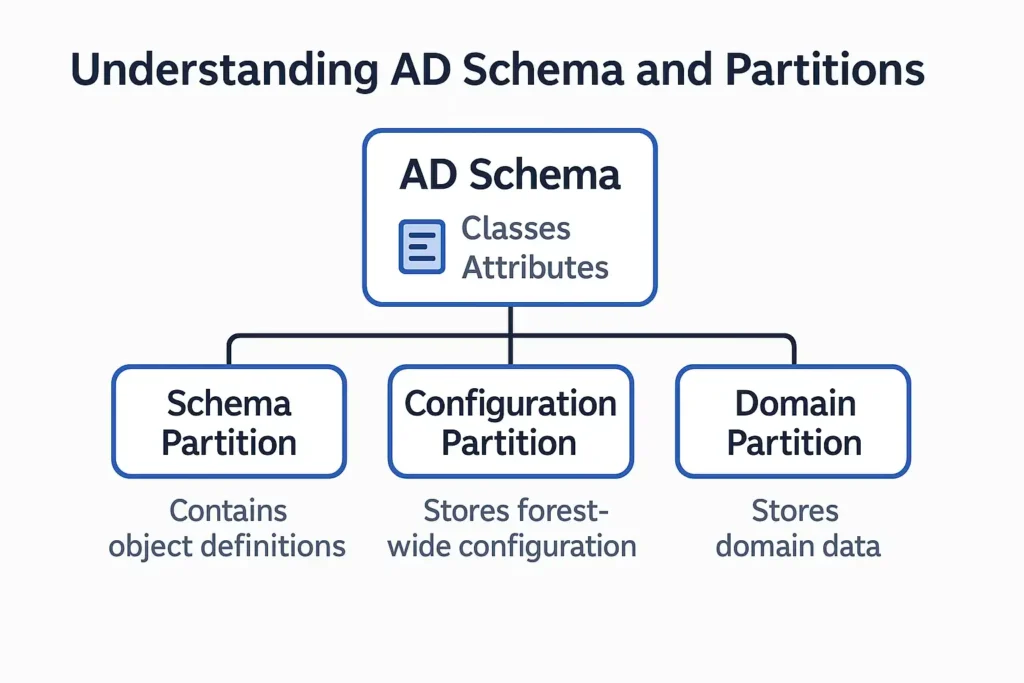
Understanding AD Schema and Partitions
The AD Schema is the definition of all objects and attributes in the directory. It acts as the blueprint of Active Directory. Every object stored in AD must follow the rules defined in the schema. For example, a user must have attributes like name, login ID, password, and group membership.
The schema consists of classes and attributes. Classes define what types of objects can exist. Attributes describe what each object can store.
AD divides data into partitions to improve performance and replication efficiency:
- The Schema Partition contains the definitions of all classes and attributes.
- The Configuration Partition stores forest-wide configuration such as sites, services, and replication settings.
- The Domain Partition stores domain-specific data like users, groups, computers, and OUs.
Active Directory Partition Structure
+-------------------------+
| FOREST |
+-------------------------+
| Schema (shared) |
| Configuration (shared) |
| Domain (per-domain)
+-------------------------+
Understanding schema and partitions is essential before extending AD for applications or designing multi-domain environments.
Planning and Deploying Active Directory
Planning is the most important phase of an Active Directory deployment. A well-designed AD environment results in better performance, easier management, and stronger security. A poorly designed one becomes difficult to maintain and fix.
The first step is network design. AD heavily relies on DNS, so selecting the right DNS namespace and ensuring proper record resolution is critical. Subnet allocation also matters, as AD uses subnets to associate clients with their nearest domain controllers.
Forest and domain design comes next. Organizations must decide whether to use a single forest or multiple forests, and how many domains are needed. A single forest with a single domain is often recommended unless administrative or legal boundaries require additional domains.
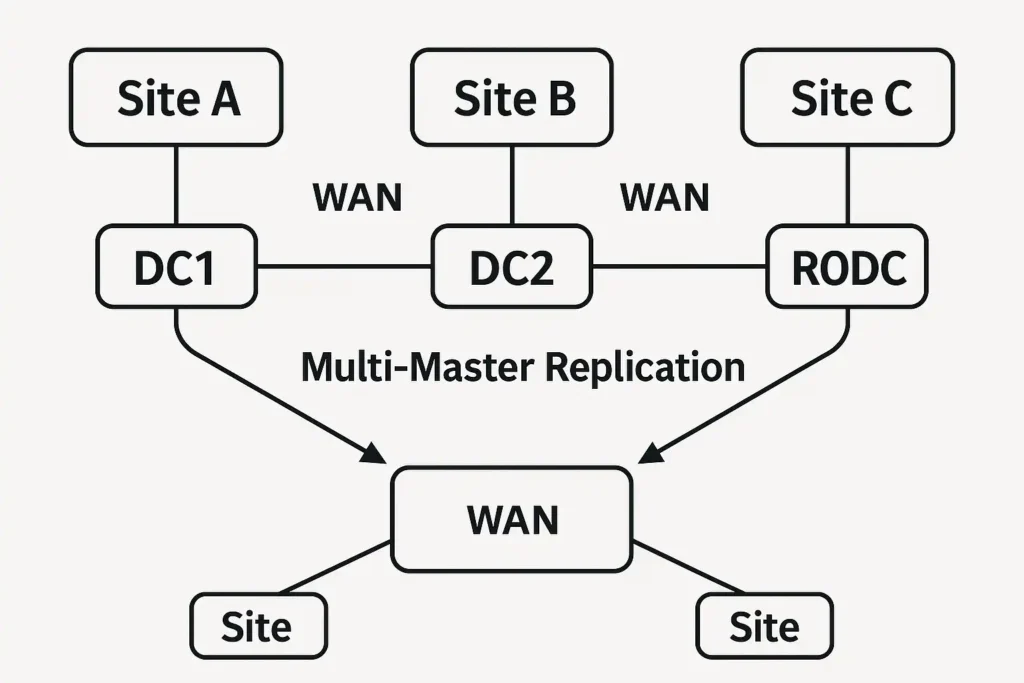
Site topology planning ensures that authentication and replication traffic flow efficiently. AD Sites represent physical locations, and domain controllers should be placed strategically to support local traffic and reduce WAN congestion.
Replication design is essential for maintaining consistency across domain controllers. AD uses multi-master replication, and administrators should define site link costs, schedules, and bridge relationships.
Deploying domain controllers requires careful consideration. Each domain should have at least two domain controllers for redundancy. Remote or low-security locations may require Read-Only Domain Controllers (RODCs). DC security must be extremely strict because they store and process sensitive identity data.
Once deployed, AD requires ongoing maintenance. This includes user and group management, permission reviews, regular health checks using tools like dcdiag and repadmin, proper backup and restore planning, patch management, and periodic security audits.
AD Site & Replication Concept Diagram
Conclusion
Active Directory remains one of the most powerful and widely used identity and access management systems in the world. Its strength lies in its ability to centralize administration, enforce security policies, and scale across complex enterprise environments. Whether integrated with modern cloud identity platforms like Microsoft Entra ID or deployed on-premises, AD continues to be essential for secure and efficient IT operations.
By understanding its components, structure, schema, partitions, replication design, and deployment best practices, administrators can build a stable, secure, and scalable identity infrastructure that will serve their organization for years to come.
Introduction to Active Directory (AD)
🎥 Learn Visually on Our YouTube Channel
Watch detailed video tutorials on Microsoft 365, Entra ID, Azure, and Active Directory directly on our BYQUS YouTube Channel. Get real-world demonstrations, Hindi explanations, and step-by-step guidance from actual admin environments.
📌 Subscribe now and never miss a new IT tutorial — from cloud configuration to troubleshooting and interview preparation.





Pingback: 5. Understanding FSMO Roles in Active Directory | Active Directory Tutorial - BYQUS – Browse Your Quick Utility & Stories
Pingback: 3. Structure of a Domain in Active Directory | Active Directory Tutorial - BYQUS – Browse Your Quick Utility & Stories
Pingback: What Is a Domain in Active Directory? A Complete Beginner-Friendly Guide - BYQUS