What Is a Forest in Active Directory? When you start learning about Active Directory (AD), you will come across many new terms — Domain, OU, Site, Trusts — and one of the most important among them is Forest. For someone who is just getting started, the word forest may sound confusing or even unrelated to technology. But don’t worry — the concept is much simpler than it seems.
Active Directory is like a structured world that helps organizations manage users, computers, and security in a centralized way. And in this world, a Forest is the biggest and most important container. It is the foundation on which everything else is built.
If you imagine Active Directory as a large house, then the forest is the entire property boundary — everything inside it belongs to you, follows your rules, and works together. Understanding the forest is the first step toward understanding how Active Directory environments are designed, organized, and secured.
In this post, we will break down this concept in the most simple and friendly way possible. No technical jargon, no complicated architecture — just a clear explanation that helps beginners understand:
- What a forest really is
- Why every Active Directory needs one
- How it helps organize domains and objects
- Why it is considered the security boundary
- How it fits into real-world company networks
By the end of this post, you will feel confident about the term Forest, and the rest of Active Directory will start making much more sense.
What Is a Forest in Active Directory?
What Is a Forest in Active Directory?
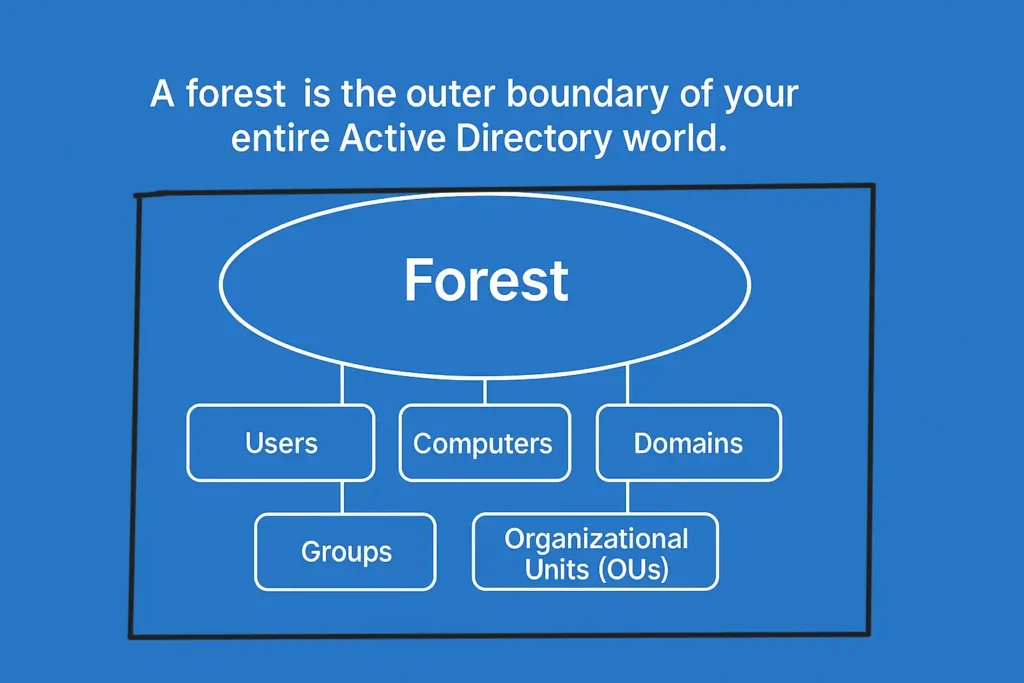
A Forest is the topmost container in Active Directory. It sits at the very highest level and defines how everything inside your Active Directory environment is organized and secured. In simple words:
A forest is the outer boundary of your entire Active Directory world.
Everything that exists inside Active Directory —
- Users
- Computers
- Groups
- Organizational Units (OUs)
- Domains
all live inside the forest.
If there is no forest, there is no Active Directory. The forest is the foundation on which everything else is built.
The Forest Is the Biggest Building Block
Imagine Active Directory as a multi-storey building full of rooms, offices, and people. The forest is the entire building itself, including the walls that protect it. Everything inside belongs to the same structure and follows the same rules.
Forest = Security Boundary
One of the most important things to understand about a forest is that it acts as a security boundary. This means the forest decides who can access what, how identities are trusted, and how information flows inside Active Directory.
Everything Inside the AD Forest Automatically Trusts Each Other
All domains inside the same forest are connected by built-in, two-way, automatic trust relationships.
This allows:
- Users in one domain to log into resources in another domain
- Groups and permissions to work across the forest
- Applications to communicate easily
You don’t need to manually configure anything — the trust is already built into the forest structure.
It’s like everyone living inside the same secure apartment building.
They move around freely because they are all part of the same community.
Anything Outside the Forest Is Separate
Domains or users from another forest:
- Do not trust your forest
- Do not have automatic access
- Cannot log in to your resources
- Cannot search for your users or groups
This separation is intentional.
A forest boundary is meant to protect your entire identity environment.
Think of it like two separate apartment buildings.
Just because someone lives in the other building doesn’t mean they can walk into yours.
Your boundary keeps things secure.
An AD Forest Contains One or More Domains
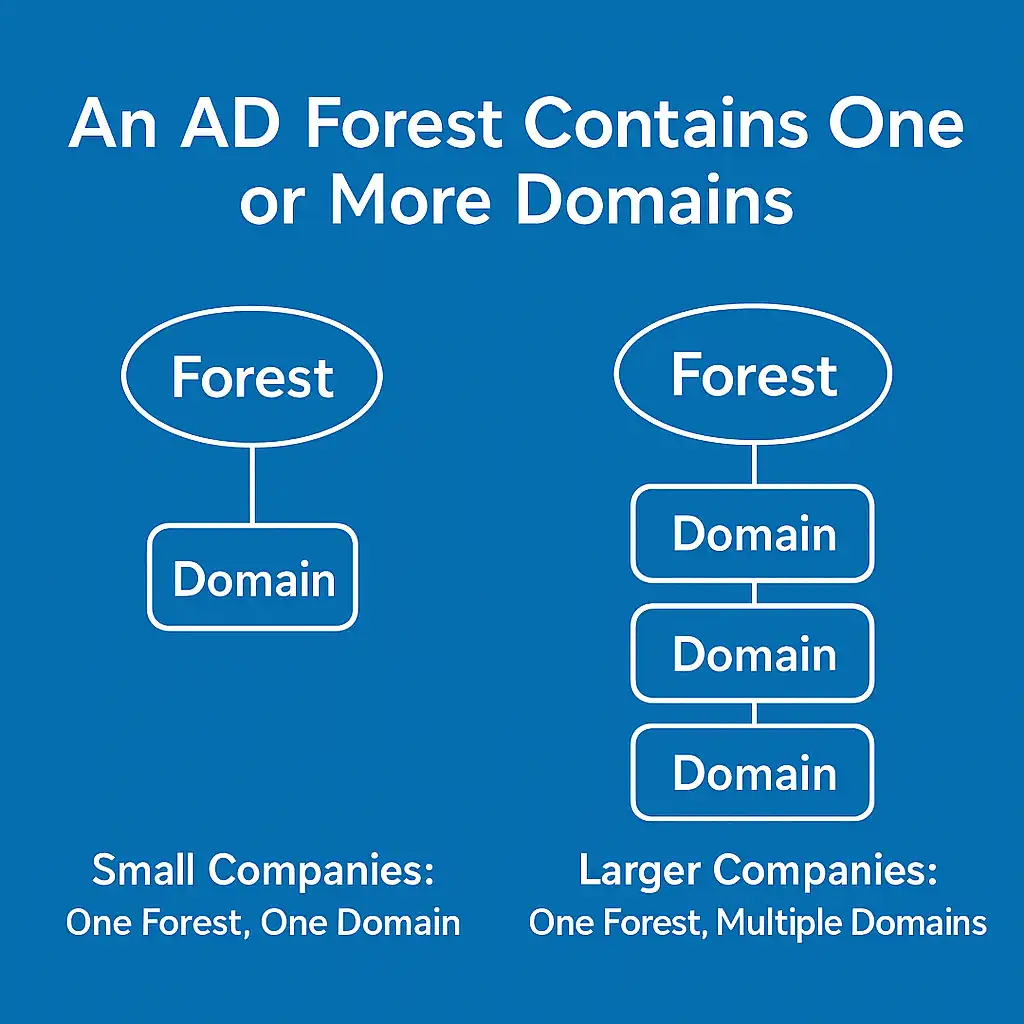
A key part of understanding a forest is knowing that it can contain one domain or multiple domains depending on how big the organization is and how they want to structure their environment.
Every Forest Has at Least One Domain
When a forest is created for the very first time, a single domain is created automatically.
This domain becomes the foundation of the forest and is called the Forest Root Domain.
But a forest doesn’t have to stop there — it can grow and include more domains if the organization needs it.
- Small companies usually have one forest + one domain
- Larger companies sometimes have one forest + multiple domains
- Very large or isolated companies may create multiple forests
Small Companies: One Forest, One Domain
Most small and medium-sized businesses keep things simple:
- One forest
- One domain
Example:
company.com
This is easy to manage, easy to understand, and more than enough for everyday needs.
Growing Companies: One Forest, Multiple Domains
As organizations expand across different regions or business units, they might choose to create additional domains inside the same forest.
For example:
company.com → Main (root) domain
india.company.com → Domain for India office
europe.company.com → Domain for Europe office
Even though these are separate domains, they all live inside the same forest, share the same structure, follow the same rules, and are part of the same identity environment.
You can think of a forest as the big container, and domains as the smaller sections inside that container.
Very Large or Isolated Organizations
Very large enterprises — especially global companies, government agencies, or companies with highly separate departments — may design multiple domains within a single forest to:
- Organize their environment better
- Separate administrative responsibilities
- Reduce complexity for different regions
But even then, all those domains are still part of the same forest boundary.
Visual Example
Imagine your company has offices in multiple countries. You may structure it like this:
company.com
india.company.com
europe.company.com
usa.company.com
All these domains are simply different branches of the same “tree” — and the entire tree lives inside one single forest.
AD Forest Shares a Common Rulebook (Schema)
Inside every Active Directory forest, there is a built-in “rulebook” called the Schema.
This schema defines the structure of Active Directory — what kinds of objects can exist and what information can be stored about them.
Think of the schema as the master guide that every domain inside the forest must follow.
What Does the Schema Do?
The schema tells Active Directory:
✔ What types of objects are allowed
These are called object classes, such as:
- User
- Computer
- Group
- Printer
- Organizational Unit (OU)
Without the schema defining them, AD wouldn’t know what a “user” or “computer” even means.
✔ What information each object can contain
These are called attributes.
For example, a user object can have attributes like:
- First Name
- Last Name
- Email Address
- Password
- Department
- Phone Number
- Job Title
A computer object may have:
- System Name
- Operating System
- Last Logon Time
Every object type has its own set of attributes, and these are all defined inside the schema.
Schema = One Rulebook for the Entire Forest
The schema is forest-wide, meaning:
- It is created once when the forest is created
- It is shared by all domains inside the forest
- Every domain follows the same object definitions and rules
No domain can have its own custom schema that differs from another domain in the same forest.
Everyone uses the same guidebook.

Why Is Schema in Active Directory Important?
Because a shared schema ensures that:
- All domains speak the same language
- All objects are stored in a consistent format
- Applications that integrate with AD work everywhere in the forest
- Searches and authentication behave the same way across the environment
In simple terms, the schema keeps the entire forest uniform and standardized.
Think of the schema like a form template.
Before filling out a form, the fields (name, email, age, etc.) must be defined.
In the same way, before creating a user or computer in AD, the schema defines exactly what fields those objects should have.
Every domain in the forest uses the same form template, so there is consistency everywhere.
Forest Shares Configuration Information
Along with sharing a common rulebook (the schema), an Active Directory forest also shares something called configuration information. This is another important part of what makes all domains inside a forest work smoothly together.
But don’t worry — it’s not complicated.
Think of configuration information as the forest-wide settings that help Active Directory understand:
- How the network is structured
- Where different locations (sites) exist
- How Domain Controllers communicate
- What services are available
- How replication should happen
These settings are stored in a special part of Active Directory called the Configuration Partition, and every Domain Controller in the entire forest receives a copy of it.
What Does Configuration Information Include?
✔ 1. Sites and Subnets
Active Directory needs to know the physical layout of your network:
- Different office locations
- Their IP subnets
- How they are connected
This helps AD direct users to the nearest Domain Controller and manage replication efficiently.
✔ 2. Replication Settings
The forest stores how Domain Controllers in different locations should communicate:
- When to replicate
- Which DCs replicate with each other
- How often replication should occur
- The type of connection between sites
This ensures that information stays updated across the entire forest.
✔ 3. Services Information
The forest also stores information about:
- What services are available
- Where they are located
- How AD-related services should behave
This helps applications and systems locate resources easily.
Why Must All Domains Share This Information?
Because without common configuration data, Active Directory would not know:
- Which domain controllers exist
- How the network is structured
- How to route authentication
- How to replicate changes
- Which domain is connected to which site
Sharing configuration information ensures smooth communication and consistent behavior across the forest.
Imagine a large company with many offices.
Configuration information is like a company map and policy handbook combined:
- The map shows where each office is located
- The handbook shows how all offices should communicate and operate
Every office has a copy of the same map and handbook, so everyone understands the structure and rules.
That’s exactly how configuration information works inside an AD forest.
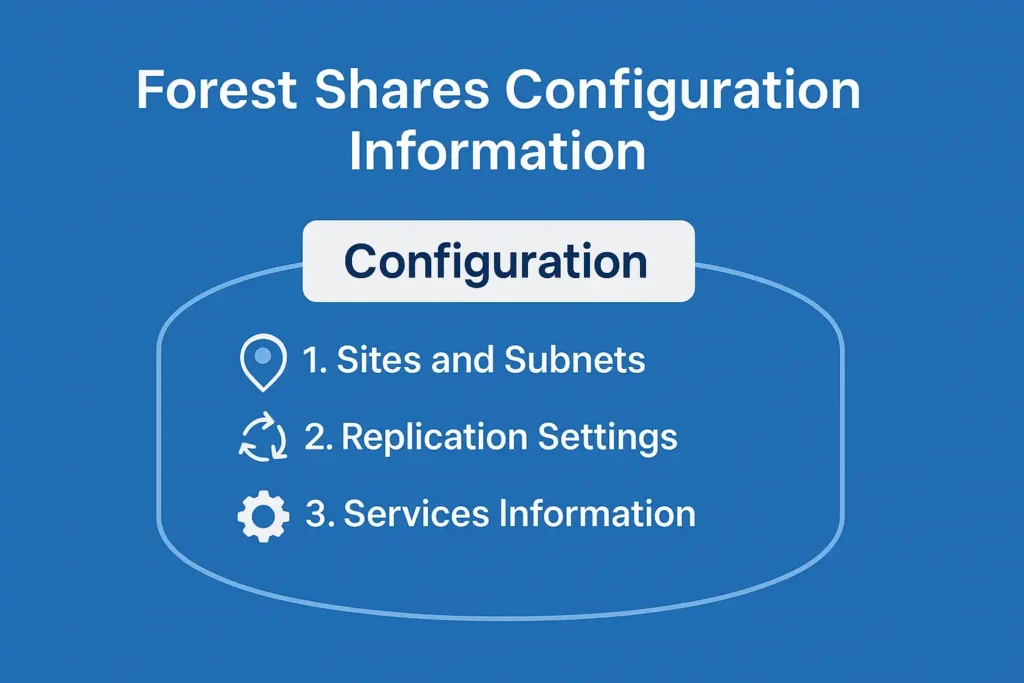
Summary
- The forest shares configuration information with all domains.
- This includes sites, subnets, services, and replication settings.
- Every Domain Controller across the forest uses this same data.
- This keeps the entire forest consistent, organized, and efficient.
The Forest Contains the Global Catalog
Another important part of an Active Directory forest is something called the Global Catalog (GC).
Beginners often find this confusing, but once you understand the idea behind it, it becomes very simple.
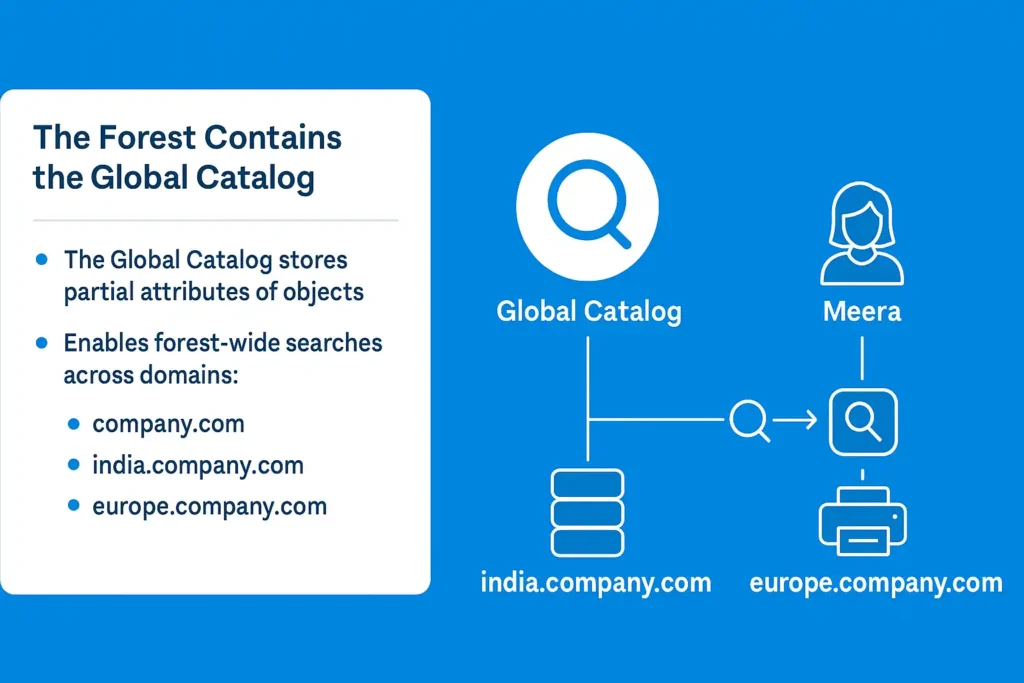
The Global Catalog is like the search engine or phonebook for the entire forest.
It helps users and applications quickly find information—even if the object they are looking for is stored in a completely different domain within the same forest.
What Does the Global Catalog Do?
The Global Catalog stores a partial copy of important attributes from every object in the forest.
This means it contains:
- Basic details about all users
- Basic details about all groups
- Basic details about all computers
- Basic details about other AD objects
Not full information — only the essential attributes needed for search and identification.
Why Do We Need a Global Catalog?
Imagine your company has multiple domains:
company.com
india.company.com
europe.company.com
Now imagine a user in the India domain wants to search for:
- Another user
- A group
- A printer
- A mailbox
- A resource in Europe
If their computer had to search each domain one by one, it would be slow and inefficient.
Instead, the Global Catalog gives one place where forest-wide information is stored.
✔ Fast searches
✔ Easy resource lookup
✔ Smooth authentication
✔ Better user experience
Simple Example
Let’s say:
- Meera works in the India domain
- She wants to find a color printer located in the Europe office
When Meera searches for the printer:
- Her computer contacts the Global Catalog server, not the Europe domain directly
- The GC quickly checks its stored information
- And returns the location of the printer
This is why we say:
The Global Catalog helps you search the entire forest from anywhere.
Any Domain Controller Can Be a Global Catalog Server
One common misconception beginners have is that:
“The Global Catalog is only stored in the Forest Root Domain.”
This is not true.
Any Domain Controller in any domain can be enabled as a Global Catalog server.
And in real-world environments, many organizations enable the GC role on:
- Most of their Domain Controllers
- All Domain Controllers in remote sites
- Or even every Domain Controller in the forest
This ensures:
- High availability
- Faster logons
- Better search performance
Why the Global Catalog Is Important?
The GC is essential for several key functions:
✔ Forest-wide search
Find users, groups, and resources across all domains.
✔ User logon (especially with universal groups)
The GC helps validate group membership for logons.
✔ Application support
Apps like Exchange, SharePoint, Skype for Business rely heavily on the GC.
✔ Cross-domain resource access
Users in one domain can locate resources in another.
Think of the Global Catalog like the index at the back of a book.
Instead of flipping through hundreds of pages to find a topic, you simply check the index, which tells you exactly where to look.
The GC works the same way — it helps you find things quickly across the entire forest.
Summary
- The Global Catalog stores important information from all domains in the forest.
- It works like a searchable phonebook or index.
- It helps users find resources anywhere in the forest.
- Any Domain Controller can be made a Global Catalog server.
- Having multiple GCs improves speed and reliability.
The First Domain = Forest Root Domain
When you create a brand-new Active Directory forest for the very first time, the very first domain you create automatically becomes the Forest Root Domain. This domain is extremely important because it acts as the foundation of the entire forest.
Think of it like building a house:
- The first domain is the ground floor.
- All other domains you add in the future are built on top of this foundation.
Without a solid ground floor, the rest of the building cannot stand strong.
Why Is the AD Forest Important?
The Forest Root Domain has a few special responsibilities:
✔ It holds certain forest-wide roles
These roles help manage:
- Schema changes
- Creation of new domains
- Forest-wide settings
These roles exist only in the forest root.
✔ It acts as the parent for other domains (if you add more)
If you add new domains later — for example, child domains like:
india.company.com
europe.company.com
They all connect back to the forest root domain.
✔ It often stores important administrative accounts
Many organizations keep their highest-level admin accounts in the forest root domain for security reasons.
The AD Forest Root Domain Should Be Stable
Because the forest root domain is the backbone of the entire forest, administrators usually keep it:
- Clean
- Stable
- Well protected
- With limited changes
Most companies avoid renaming or restructuring the forest root domain because it affects the entire AD environment.
Imagine a big tree:
- The forest is the land where all the trees grow
- The forest root domain is the main trunk
- Any additional domains are the branches
- All branches depend on the trunk
If the trunk is strong and stable, the whole tree stays healthy.
Summary
- The first domain you create in a forest becomes the Forest Root Domain.
- It holds special forest-wide roles and responsibilities.
- All future domains connect back to it.
- It should remain stable and well-managed.

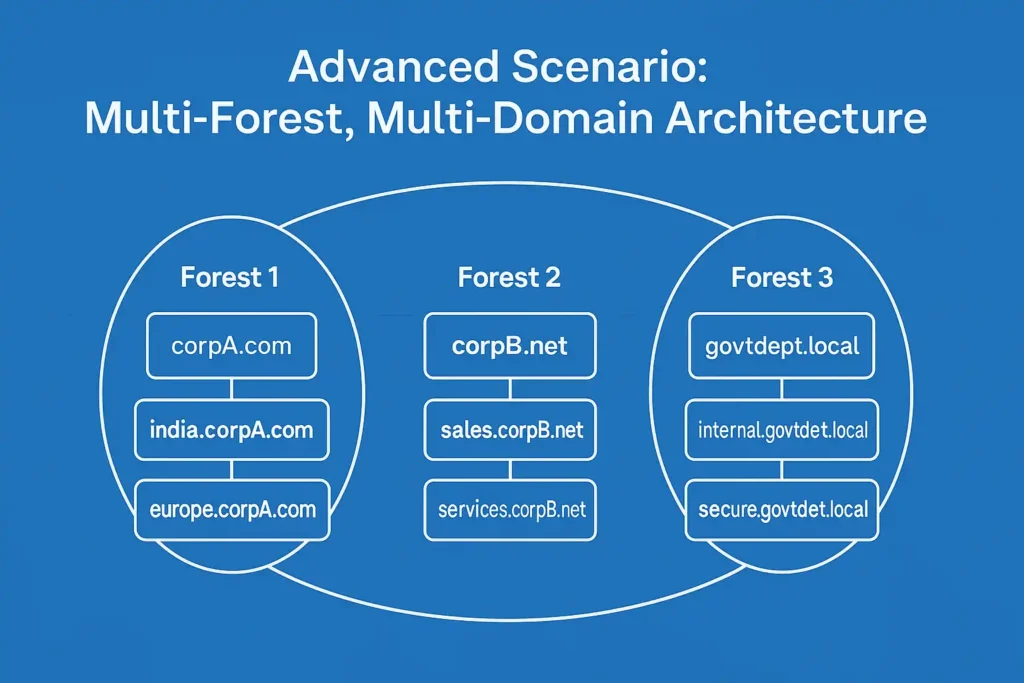
Advanced Scenario: Multi-Forest, Multi-Domain Architecture
While most organizations use one forest (with one or more domains), there are situations where companies operate multiple forests, each containing its own set of domains. This is known as a Multi-Forest, Multi-Domain architecture.
This design is not common for everyday environments, but it is used when strict separation is required.
✔ When Does This Happen?
Organizations may choose a multi-forest model when they need:
- Complete security isolation between departments or business units
- Different IT teams managing their own identity systems independently
- Legal or compliance requirements that prevent sharing identity data
- Acquired companies that must keep their existing AD structure
- Different schemas or configurations that cannot be combined
In these cases, each forest becomes its own independent identity world, with its own:
- Domains
- Administrators
- Security policies
- Global Catalog servers
- Schema and configuration
If collaboration is required between forests, special trusts are created, but by default these forests remain fully separate.
🧩 Simple Example of Multi-Forest, Multi-Domain Architecture
Imagine a large global group with three independently operated companies:
- Forest 1: corpA.com
- Domains: india.corpA.com, europe.corpA.com
- Forest 2: corpB.net
- Domains: sales.corpB.net, services.corpB.net
- Forest 3: govtdept.local
- Domains: internal.govtdept.local, secure.govtdept.local
Each forest operates separately.
Each one has its own security boundary.
They only communicate if a trust relationship is set up—otherwise they behave like completely different environments.
🎯 Beginner Summary
- A single forest is recommended for most companies.
- Large organizations may use multiple domains inside one forest.
- Multi-Forest, Multi-Domain is used only when strict separation is required.
- Each forest acts as an independent identity system unless connected using a trust.
Conclusion
An AD Forest is the highest and most important structure in Active Directory. It acts as the security boundary, the organizational framework, and the foundation for everything that exists inside AD. Whether you have one domain or many, the forest ties them all together under one unified identity system.
Inside a forest, all domains share the same schema, the same configuration information, and have access to the Global Catalog, which makes searching and authentication fast and efficient. This shared structure ensures consistency, stability, and smooth communication across the entire environment.
If you understand what a forest is —
how it works, what it contains, and why it exists —
you’ve already taken a big step toward understanding the bigger world of Active Directory.
From here, concepts like Domains, Sites, Organizational Units (OUs), Trusts, and Group Policies will start making much more sense. Keep following this series as we continue to simplify every part of Active Directory for beginners.
What Is a Forest in Active Directory?
🎥 Learn Visually on Our YouTube Channel
Watch detailed video tutorials on Microsoft 365, Entra ID, Azure, and Active Directory directly on our BYQUS YouTube Channel. Get real-world demonstrations, Hindi explanations, and step-by-step guidance from actual admin environments.
📌 Subscribe now and never miss a new IT tutorial — from cloud configuration to troubleshooting and interview preparation.
Frequently Asked Questions About Active Directory Forests
1. What is a Forest in Active Directory?
A Forest is the topmost container in Active Directory. It defines the overall security boundary and the highest level of organization. Everything inside Active Directory — users, computers, groups, OUs, and domains — exists within a forest.
2. Why is the Forest considered a security boundary?
The forest acts as an isolation boundary. Domains inside the same forest automatically trust each other, while different forests are separate by default. Cross-forest access requires explicit trusts or federation, ensuring strict security separation.
3. How many domains can a forest contain?
A forest must contain at least one domain (called the Forest Root Domain), but it can contain multiple domains.
Small companies typically use one domain, while larger organizations may create several domains for different regions or administrative divisions — all under the same forest.
4. What is the Schema and who uses it?
The Schema is the forest-wide rulebook that defines all object types — such as user, computer, group, printer, and OU — and the attributes they can contain.
Every domain in the forest follows the same schema, ensuring consistent object structure and behavior across the entire environment.
5. What is the Global Catalog and why is it important?
The Global Catalog (GC) stores a partial copy of key attributes from every object in all domains within the forest.
It enables fast, forest-wide searching and supports key authentication processes, including universal group membership lookups. Without the GC, cross-domain queries would be slow and inefficient.
6. What is the Forest Root Domain?
The Forest Root Domain is the first domain created when a new forest is built.
It holds forest-wide roles such as the Schema Master and the Domain Naming Master, and it acts as the foundation for all additional domains added to the forest.
Because of its importance, the forest root domain should remain stable and well-protected.
7. When should organizations use multiple forests?
Multiple forests are used only when strict security, legal, or administrative isolation is required.
Examples include government departments, separate companies under the same group, regulated industries, or acquired companies that must maintain their own identity system.
Multi-forest designs are more complex and should be used only when necessary.
8. Does the Global Catalog have to run on domain controllers in the Forest Root Domain?
No.
Any domain controller in any domain within the forest can be enabled as a Global Catalog server.
Most organizations deploy GC on multiple Domain Controllers for redundancy and improved performance, especially in distributed environments.





Pingback: What Is a Domain in Active Directory? A Complete Beginner-Friendly Guide - BYQUS